-
Notifications
You must be signed in to change notification settings - Fork 3
AD UserPasswordAudit
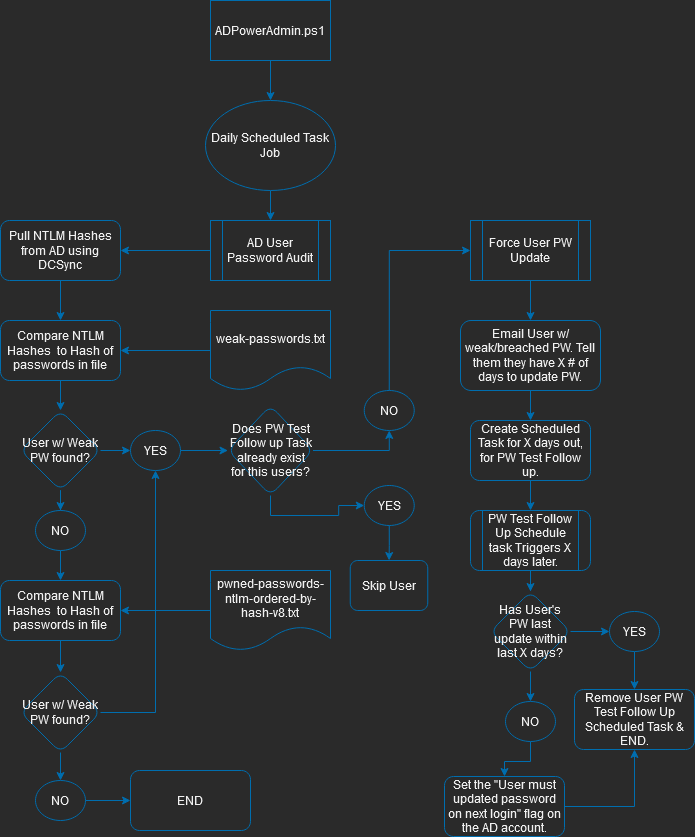
The Password Audit checks for the following.
- Weak or breached passwords.
- Groups of User accounts that all have the same password.
- User accounts will never expire.
- Administrative accounts are allowed to be delegated to a service account.
If you want to test for known breached passwords, you will need to download the breached password list from https://haveibeenpwned.com/Passwords. The file is a 7z compressed file. You will need to extract the file and save it to the same directory as the AD-PowerAdmin.ps1 script. The file name should be 'pwned-passwords-ntlm-ordered-by-hash-v8.txt' and the file size should be 28.5GB uncompressed. The file is updated every 12 months. You will need to download the new file and replace the old file when it is updated.
If you want to test for weak passwords, you will need to download or build a list of weak passwords.
The file should be a text file with one password per line. Consider all the bad passwords you have seen in
the past within your company and add them to the list. This will help prevent users from using these very
bad passwords. Every company is guilty of using bad passwords with the company name in it, or the name of
the CEO, or the name of the company mascot, etc.
Example: '<CompanyName>2022!', '<CompanyInitials>2022!', '<CompanyHqCityName>@<YearEstablished>', etc.
The file name should be 'weak-passwords.txt' and reside in the same directory as the AD-PowerAdmin.ps1 script.
Users will be notified via email if their password is weak or breached. User accounts with a weak or breached password will have X days to change their password, default is 3 days. If the user does not change their password within X days, the user account will have the 'User must change password at next logon' option enabled.
On the first day of the month, the script will send an email to the admin account with a report of all the audit results.
- You must update the settings in 'AD-PowerAdmin_settings.ps1' to matches your AD setup.
- The follow up process to ensure users change their password is done via a scheduled task.
- The process by which the password data is pulled is done via a DCSync. This can trigger an alert in your SIEM. A DCSync, is not an attack, it is a normal process, but attackers are known to use DCSync to get password hashes.
- If non-user accounts have the warning 'These administrative accounts are allowed to be delegated to a service' then it may be a false positive. See my post here for more details: https://cybergladius.social/@CyberGladius/109649278142902592